A critical vulnerability tracked as CVE-2024-34359 and dubbed Llama Drama can allow hackers to target AI product developers.

Our research reveals that personal repositories often expose sensitive corporate data, leading to severe security breaches

Security researchers discovered two previously unseen backdoors dubbed LunarWeb and LunarMail that were used to compromise a European government's diplomatic institutions abroad.

New versions of Git are out, with fixes for CVE-2024-32002, which can be used to remotely execute code during a "clone" operation.

The North Korean hacker group Kimsuki has been using a new Linux malware called Gomir that is a version of the GoBear backdoor delivered via trojanized software installers.

Microsoft Threat Intelligence has observed Storm-1811 misusing the client management tool Quick Assist to target users in social engineering attacks that lead to malware like Qakbot followed by Black Basta ransomware deployment.

Plenty of patches for everyone, even if your product doesn’t include the zero-day fix.

Exploit code is circulating for CVE-2024-4761, disclosed less than a week after a similar security vulnerability was disclosed as being used in the wild.

Recorded Future details a novel campaign that abuses legitimate internet services to deploy multiple malware variants for credential theft

Organizations continue to run insecure protocols across their WAN, making it easier for cybercriminals to move across networks.

In Cambodia, Laos and Myanmar, the groups are estimated to reap about $43.8 billion each year through scams — some 40 percent of the three nations’ combined formal GDP.

Today is Microsoft's May 2024 Patch Tuesday, which includes security updates for 61 flaws and three actively exploited or publicly disclosed zero days.

VMware fixed four security vulnerabilities in the Workstation and Fusion desktop hypervisors, including three zero-days exploited during the Pwn2Own Vancouver 2024 hacking contest.

For the benefit of the cybersecurity community and network defenders—and to help every organization better manage vulnerabilities and keep pace with threat activity—CISA maintains the authoritative source of vulnerabilities that have been exploited in the wild. Organizations should use the KEV catal...
On May 10, 2024, Phylum’s automated risk detection platform alerted us to a suspicious publication on PyPI. The package was called requests-darwin-lite and appeared to be a fork of the ever-popular requests package with a few key differences, most notably the inclusion of a malicious Go binary packe...

The wide-ranging hacking campaign by the state-backed group Volt Typhoon is seen as a prelude of what's to come.

Pro-Russia hackers targeted government websites in Kosovo in retaliation for the government's support to Ukraine with military equipment.

The notorious FIN7 hacking group is at it again! This time, they're using malicious Google ads to trick users into downloading malware disguised as le

Researchers have uncovered a new attack called "LLMjacking" that targets large language models (LLMs) hosted on cloud services.
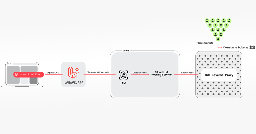
Researchers recently spotted the Spanish-speaking threat actor —with nearly 400 previous victims under its belt — in a new campaign in Latin America and Central Africa.

IoCs available in the original article.
Please note that the attack can only be carried out if the local network itself is compromised.

IoCs available here. Some of them with no detection on VT.
MS involved. Again.
Of course, in the end it is just conflict, and when it spills over into the real world then you have a war. But this is not always the case We have already had disruption in power grids, nuclear plants, hospitals, public offices, critical infrastructure of financial markets (some of them with impact in real lives) without retaliation in the physical world.
Cyberwar, in my perspective, have some nuances. For instance, in a physical conflict, a hostile nation's invasion of my property immediately becomes a state issue. However, this isn't always the case in a cyberwar if a hostile state invades my organization (It's hard to immediately distinguish whether the actor is a nation state, a financially motivated group, hacktivists, or just a guy who eats pizza in his mom's basement). Most of the time, organizations are on their own.
In a cyberwar, espionage is also far more acceptable. This is something the NSA (and FSB/SVR) has been doing for years (against private entities and states). In a way, I understand that it is something similar to what the cold war was (is), but with no boots on the ground.
I'd better say that states have been doing this.
Cyber war, of course. I think that there is a cyber war going on for quite some time now. CWWI (Cyber World War I).
If anyone is still using it, anyways....
Maybe cyber resilience? Quick identify, respond and recover from an incident.
Hackers 10 - 1 LastPass
From the article:
Microsoft locked down a server last month that exposed Microsoft employee passwords, keys and credentials to the open Internet, as the company faces growing pressure to strengthen the security of its software. Microsoft was notified of the vulnerability on February 6th and the block on March 5th. It is unclear whether anyone accessed the exposed server during this period.
In this particular case, the method of infection of the router was not disclosed. However, typically, the most common methods involve an open administration port to the internet (user interface or TR-069) or through the internal interface, in case a network host has been compromised.
They often perform brute-force password attacks, and once access is obtained, they look for typical Linux administrative tools (such as bash, etc.) and proceed to compromise the router.
So I understand that a router with custom firmware can be compromised if it has a weak password and resources to maintain the infection, or of course, a vulnerability that is exploitable.
Stop giving me your toughest battles <insert meme here>
IoCs from original research:
Hashes
267071df79927abd1e57f57106924dd8a68e1c4ed74e7b69403cdcdf6e6a453b 54/70
d6ac21a409f35a80ba9ccfe58ae1ae32883e44ecc724e4ae8289e7465ab2cf40 54/71
ad4d196b3d85d982343f32d52bffc6ebfeec7bf30553fa441fd7c3ae495075fc
13c017cb706ef869c061078048e550dba1613c0f2e8f2e409d97a1c0d9949346
b376a3a6bae73840e70b2fa3df99d881def9250b42b6b8b0458d0445ddfbc044
Domains
hanagram[.]jpthefinetreats[.]com
caduff-sa[.]chjeepcarlease[.]com
buy-new-car[.]com
carleasingguru[.]com
IP Addresses
91[.]193[.]18[.]120
Link to article.
IoCs:
IOCs Hashes (SHA-256) Email – 16e6dfd67d5049ffedb8c55bee6ad80fc0283757bc60d4f12c56675b1da5bf61
Docx – 1abf56bc5fbf84805ed0fbf28e7f986c7bb2833972793252f3e358b13b638bb1
Injected ZIP – 95898c9abce738ca53e44290f4d4aa4e8486398de3163e3482f510633d50ee6c
LNK file – d07323226c7be1a38ffd8716bc7d77bdb226b81fd6ccd493c55b2711014c0188
Final ZIP – 94499196a62341b4f1cd10f3e1ba6003d0c4db66c1eb0d1b7e66b7eb4f2b67b6 26/64
Client32.exe – 89f0c8f170fe9ea28b1056517160e92e2d7d4e8aa81f4ed696932230413a6ce1 26/73
URLs and Hostnames yourownmart[.]com/solar[.]txt
firstieragency[.]com/depbrndksokkkdkxoqnazneifidmyyjdpji[.]txt
yourownmart[.]com
firstieragency[.]com
parabmasale[.]com
tapouttv28[.]com
IP Addresses 192[.]236[.]192[.]48
173[.]252[.]167[.]50
199[.]188[.]205[.]15
46[.]105[.]141[.]54
Others Message ID contains: “sendinblue[.]com”
Return Path contains: “sender-sib[.]com”
For the IoCs, check the original research.
Normally web filters categorize IPFS gateways as p2p, and most organizations block this category.